Microsoft Azure Data Engineering Training Cou ...
- 16k Enrolled Learners
- Weekend
- Live Class
In my previous blog, I spoke about 3 Knowledge objects: Splunk Timechart, Data model and Alert that were related to reporting and visualizing data. In this blog, I am going to explain Splunk Events, Event types, and Splunk Tags. These knowledge objects help to enrich your data in order to make them easier to search and report on. Learn all about Splunk with the Splunk Certification.
So, let’s get started with Splunk Events.
An event refers to any individual piece of data. The custom data that has been forwarded to Splunk Server are called Splunk Events. This data can be in any format, for example: a string, a number or a JSON object.
Let me show you how events look in Splunk:
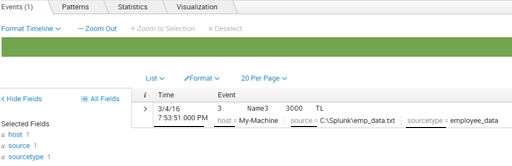
As you can see in the above screenshot, there are default fields (Host, Source, Sourcetype and Time) which gets added after indexing. Let us understand these default fields:
Now, let us learn how Splunk Event types help you to group similar events.
Assume you have a string containing the employee name and employee ID and you want to search the string using a single search query rather than searching them individually. Splunk Event types can help you here. They group these two separate Splunk events and you can save this string as a single event type (Employee_Detail).
Do note that you cannot use a pipe character or a sub search while defining an event type. But, you can associate one or more tags with an event type. Now, let us learn how these Splunk event types are created.
There are multiple ways to create an event type:
Let us go into more detail to understand it properly:
1. Using Search: We can create an event type by writing a simple search query.
Go through the below steps to create one:
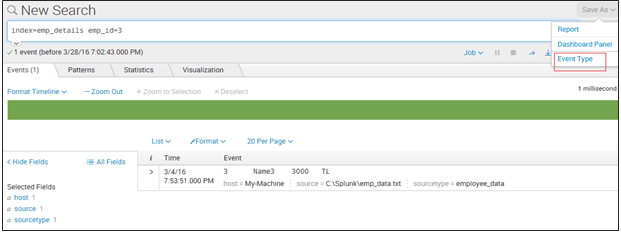
> Run a search with the search string
For Example: index=emp_details emp_id=3;
> Click Save As and select Event Type.
You can refer to the below screenshot to get a better understanding:
2. Using Build Event Type Utility: The Build Event Type utility enables you to dynamically create event types based on Splunk events returned by searches. This utility also enables you to assign specific colors to event types.
You can find this utility in your search results. Let’s go through the below steps: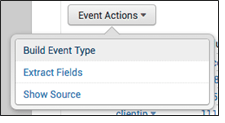
Step1: Open the dropdown event menu
Step2: Find the down arrow next to the event timestamp
Step3: Click Build event type
Once you click on ‘Build Event Type’ displayed in the above screenshot, it will return the selected set of events based on a particular search.
3. Using Splunk Web: This is the easiest way to create an event type.
For this, you can follow these steps:
» Go to Settings
» Navigate to Event Types
» Click New
Let me take the same employee example to make it easy.
Search query would be same in this case:
index=emp_details emp_id=3
Refer to the below screenshot to get a better understanding: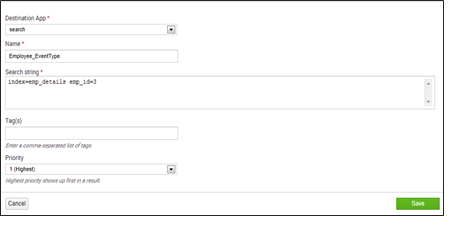
4. Configuration files (eventtypes.conf): You can create event types by directly editing eventtypes.conf configuration file in $SPLUNK_HOME/etc/system/local
For Example: “Employee_Detail”
Refer to the below screenshot to get a better understanding:

By now, you would have understood how event types are created and displayed. Next, let us learn how Splunk tags can be used and how they bring clarity to your data.
Splunk Tags
You must be aware of what a tag means in general. Most of us use the tagging feature in Facebook to tag friends in a post or photo. Even in Splunk, tagging works in a similar fashion. Let’s understand this with an example. We have an emp_id field for a Splunk index. Now, you want to provide a tag (Employee2) to emp_id=2 field/value pair. We can create a tag for emp_id=2 which can now be searched using Employee2.
Look at the screenshot on right side to create a Splunk tag.
Go to Settings -> Tags
Now, you might have understood how a tag is created. Let us now understand how Splunk tags are managed. There are three views in Tag Page under Settings:
1. List by field value pair
2. List by tag name
3. All unique tag objects
Let us get into more details and understand different ways to manage and get quick access to associations that are made between tags and field/value pairs.
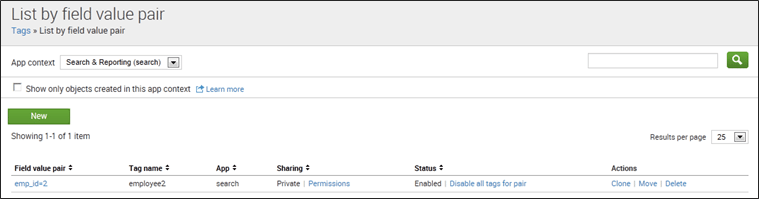
1. List by field value pair: This helps you to review or define a set of tags for a field/value pair. You can see the list of such pairings for a particular tag.
Refer to the below screenshot to get a better understanding:
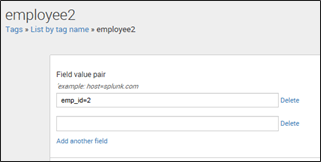
2. List by tag name: It helps you to review and edit the sets of field/value pairs. You can find the list of field/value pairing for a particular tag by going to ‘list by tag name’ view and then click on the tag name. This takes you to the detail page of the tag.
Example: Open the detail page of employee 2 tag.
Refer to the below screenshot to get a better understanding:
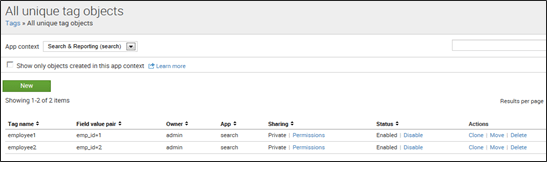
3. All unique tag objects: It helps you to provide all the unique tag names and field/value pairings in your system. You can search a particular tag to quickly see all the field/value pairs with which it’s associated. You can easily maintain the permissions, to enable or disable a particular tag.
Refer to the below screenshot to get a better understanding:
Now, there are 2 ways to search tags:
In this blog, I have explained three knowledge objects (Splunk events, event type and tags) that help to make your searches easier. In my next blog, I will explain some more knowledge objects like Splunk fields, how field extraction works and Splunk lookups. Hope you enjoyed reading my second blog on knowledge objects.
 Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUPedureka.co