Cyber Security and Ethical Hacking Internship ...
- 15k Enrolled Learners
- Weekend/Weekday
- Live Class
Fundamentally, social engineering is not the same as a cyberattack. Rather, social engineering relies heavily on the psychology of convincing, attacking the mind like a classic with artists. The idea is to win targets over to the idea that you are trustworthy so they will let down their defenses and be more likely to engage in risky behavior, like disclosing personal information, opening potentially malicious attachments, or clicking on web links.
Even though recovering from a social engineering attack is much more difficult, preventing one can have far less disastrous effects. It’s critical to be watchful and take proactive steps in order to protect your company and its reputation.
We’ll go over everything you need to know in this blog, including:
Instead of using forceful hacking to access systems or data, social engineering leverages human psychology. The criminal deceives victims into clicking on malicious links by playing on human emotions like fear, curiosity, pride, and anger.
Social engineering attacks coerce their victims into divulging private information or carrying out predetermined actions. In order to obtain the background knowledge needed for the next attack, such as potential points of access and lax security measures, the attacker first looks into the intended victim.
Now that you have a clear understanding of social engineering, we’ll move on to how it works.

Social engineering is the practice of using psychological characteristics and social norms to coerce people or organizations into disclosing private information, acting in a certain way, or granting access to protected systems. This is how it usually works:
Research: Assailants obtain data about their target, including personal information, organizational configuration, and security guidelines. This could entail searching through public databases, company websites, and social media profiles to create a profile of the target and find any vulnerabilities.
Building Trust: To establish rapport and win their targets’ trust, attackers employ a variety of strategies. This can entail assuming the identity of a high-ranking individual, like an IT support staff member, business executive, or reliable service provider. Attackers can manipulate their targets by taking advantage of human emotions such as trust, fear, or curiosity by using social engineering techniques.
Creating a Pretext: To make their demands appear reasonable, attackers fabricate a story or scenario. This can entail taking on the persona of a helpless coworker, a distressed client, or an official from a reliable company. By creating a compelling backstory and including supporting details, attackers can make their targets more likely to comply with their requests.
Requesting Information or Action: After establishing trust and creating a pretext, attackers proceed to extract sensitive data or influence their targets to take specific actions. This could entail coercing targets into downloading malware or clicking on nefarious links, or it could entail requesting login information, account numbers, or other private information.
Exploiting Vulnerabilities: Once the target’s compliance and trust have been established, attackers take advantage of vulnerabilities to further their goals. This might entail stealing confidential data, breaking into accounts or systems without authorization, or launching more assaults against the target or their company.
Social engineering is effective because it takes advantage of basic human tendencies like empathy, trust, and the desire to be helpful or cooperative. Attackers can effectively manipulate their targets into disclosing information or taking actions that compromise security by being aware of these psychological characteristics and social norms.
Also Read: What is CISSP Certification?
We’ll talk about the typical social engineering attack now.
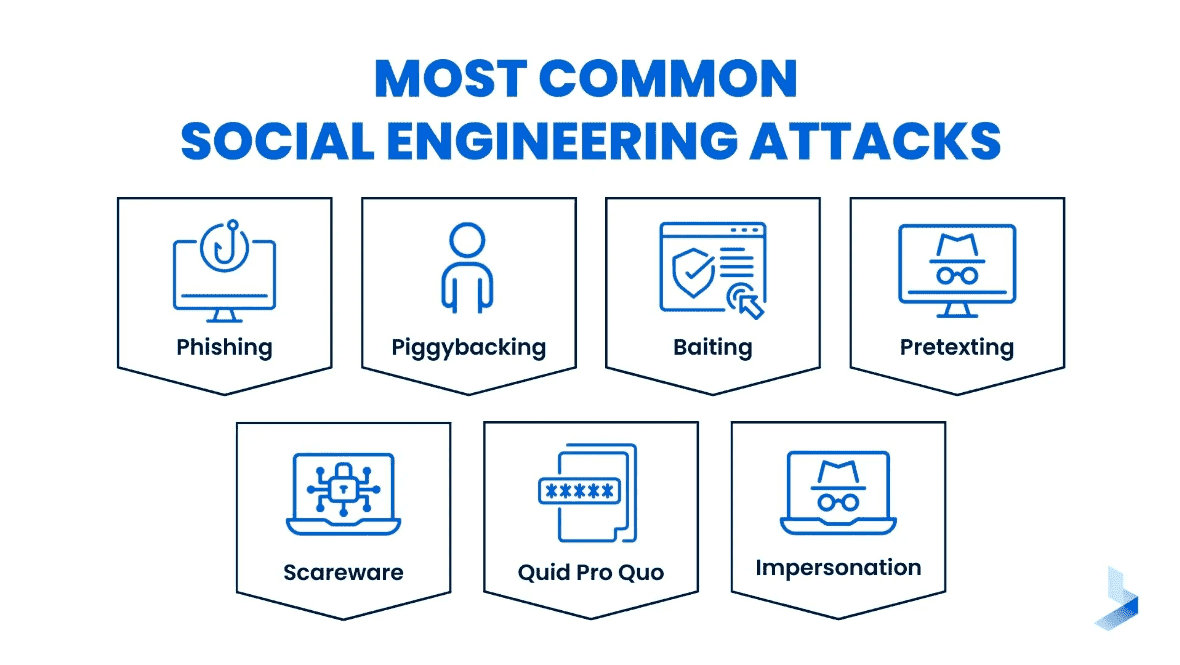
The most popular and effective kind of social engineering attack is phishing. To trick Someone or an organization into disclosing their personal information and other valuables, the criminal uses email, chat, web ads, and websites.
For instance, the perpetrator might pose as a representative of a bank, a government agency, or a significant company that the victim knows and trusts. One possible source could be an email asking users to click on a link to access their accounts. After users are redirected there, the attack takes place on a spoof website that looks legitimate.
A more focused type of phishing is called spear phishing. In an effort to fool the target into thinking they are connected to the sender, the scammer tailored their attack emails with the target’s name, position, phone number, and other details.
For example, imagine getting an email purporting to be from the CEO of your business asking for quick attention to a private project. Given that it uses your name and alludes to internal information, the email is legitimate. In an attempt to comply, you click on the attached document, inadvertently causing the malware to infiltrate your company’s network and displaying a targeted spear phishing attack that employs individualized data to deceive and damage particular people or companies.
The term “baiting” in cybersecurity describes enticing people to divulge personal information or device access in exchange for something significant, like free software or media. This usually takes the form of dispersing malicious CDs, USB drives, or other media in public areas in an attempt to exploit people’s curiosity about security flaws.
For example, To engage in cybersecurity baiting, one can place a USB drive marked “Confidential Project Plans” on a cafeteria table and wait for a curious employee to pick it up and plug it into their computer.
A form of social engineering known as “voice phishing” or “vishing” involves using phone calls to deceive victims into divulging personal information or acting on it.
For example, An attacker could pose as a bank representative and ask for the victim’s account details and verification codes while claiming there is a security breach.
A malicious program or application known as “scareware” tricks people into thinking their computer is infected with malware or viruses. Usually, it offers to remove the alleged threats by purchasing phony antivirus software or services from the user. Actually, the danger comes from scareware itself, which is often made to infect computers with malware or steal money from unsuspecting victims.
For example, a pop-up message that informs a user that their computer has multiple viruses and requests that they download and install a particular antivirus program immediately to eliminate the threats is known as scareware. Nevertheless, opening the pop-up window or following the directions would damage the user’s computer by installing malicious software, harming its security, and stealing sensitive information.
Pretexting is the practice of an attacker fabricating a situation or pretext to coerce a target into disclosing information or taking actions against their better judgment. This frequently entails pretending to be an official, like an IT support staff member or an executive of the company.
For example, Someone may call you on the phone posing as from your bank’s fraud department, requesting account information because they’ve noticed some unusual activity. You may give them the information because you think they’re real, only to find out later that it was a scam. This is a prime illustration of pretexting.
Attackers who use quid pro quo tactics provide something of value in return for sensitive data or access.
For example, Under the guise of IT support, an attacker requests login credentials in exchange for free software upgrades. Workers give their credentials because they are excited about the upgrade and don’t realize they are being duped. The attacker demonstrates a quid pro quo attack by using this information to obtain unauthorized access.
Tailgating, also referred to as piggybacking, is the act of physically trailing Someone into a restricted space or structure without their permission. Attackers take advantage of people’s innate desire to be courteous to others and to hold doors open for them.
For example, As you enter your office building using your access badge, a person walks up behind you and asks you to hold the door open for them because they can’t find their badge. Assuming they’re coworkers, you comply. But once inside, they don’t go through security checks and are free to move around. This is an example of tailgating—unauthorized people entering by taking advantage of other people’s courtesy.
You are now aware of the attacks that will be launched against you. How can I protect myself and my company from social engineering?
In order to safeguard your company and yourself from social engineering, you must first implement security measures, educate others, and create awareness. Here are some tactics:
Employee Awareness and Training: Organize frequent training sessions to inform staff members about typical social engineering tactics such as vishing, phishing emails, and fake news. Teach them to recognize and verify communications, verify the accuracy of requests, and report any unusual behavior right away.
Execute Robust Security Guidelines: Create and implement robust safety procedures and controls, such as data handling guidelines, access controls, and password management. To lessen the possibility of sensitive information being accessed or disclosed without authorization, ensure staff members are aware of and abide by these policies.
Multi-factor authentication (MFA):should be implemented on all systems and applications in order to provide an extra layer of security on top of passwords. Even if users’ passwords are compromised, they are required to provide additional authentication factors, like a temporary code sent to their mobile device, to verify their identity and stop unwanted access.
Frequent Security Assessments: To find and fix possible weaknesses in your company’s procedures, controls, and organizational structures, conduct regular security assessments, including vulnerability analyses and hacking tests. Take proactive steps to identify and mitigate security risks before attackers can exploit them.
Keep yourself informed and current: Stay current about the most recent social engineering techniques and cybersecurity risks by following industry news, signing up for safety alerts, and participating in relevant forums or communities. Apply the most recent patches and updates to software and security tools to guarantee protection against known vulnerabilities.
Also Read: Benefits of Ethical Hacking For Organizations
We’ll now examine the reason. Why do online fraudsters employ social engineering techniques?
In recent years, social engineering has gained popularity among cybercriminals as an attack technique. It has proven to be the most successful way for a criminal to “inside” a company.
Cybercriminals are using increasingly intricate human hacking schemes. A social engineer gathers as much information as possible about an individual or company. This can entail looking up the target’s information online or on social media.
To stay safe from social engineers’ dangers, you must be vigilant, educate yourself, and know their tricks. A business email breach could severely impact your company.
Let’s examine Why social engineering poses such a risk.
Social engineering is particularly dangerous because its attacks don’t always have to target the entire organization; if a victim is successfully tricked, they can provide enough information to start an attack that takes down the organization as a whole.
Social engineering attacks have grown increasingly sophisticated over time. Social engineering has become a popular technique used by attackers to bypass an organization’s initial defenses and cause further confusion and harm. Fake websites and emails not only seem convincing enough to fool victims into divulging personal information that can be used for identity theft.
Let’s examine some best practices for preventing attacks using social engineering.
Take care of what you divulge. Furthermore, you don’t need to be afraid of these attacks. You can take steps to avoid them. Here are a few methods to assist.
Identifying the warning indicators and avoiding attacks is one of the best defenses against social engineering. Several indicators of concern include:
We hope this has improved your understanding of social engineering and all the risks involved. But you can only be sure whether you will withstand a significant breach once you test your security posture.
Social engineering poses a serious risk in the modern digital environment. Attackers can circumvent even the strongest technological defenses by taking advantage of human psychology. However, people and organizations can greatly lower their risk by being aware of social engineering, how it operates, and how to prevent it. Adopting a proactive approach to social engineering is not only advisable but also imperative, given that people are frequently the weakest link in systems.
Our blog post about social engineering in cyber security is now complete. I hope I made all the key points in this blog clear. The Edureka Certified Ethical Hacking Course – CEH v12, is the most recent course to learn and offers practical training, Edureka and EC-Council have partnered to provide you with the chance to obtain the widely accepted CEH v12 certification. This ethical hacking certification course focuses on fundamental cybersecurity abilities necessary for network and security analysts. To become a Certified Ethical Hacker (CEH), the CEH training is intended to verify your proficiency in subjects like network security, session hijacking, cryptography, and more.
Have you got a question for us? Please let us know by leaving a note in the comments section, and we will contact you.
 Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUPedureka.co