Cyber Security and Ethical Hacking Internship ...
- 15k Enrolled Learners
- Weekend/Weekday
- Live Class
Similarly, when you know about your target, half the task of Hacking is done. There are different ways to gather information about your target. In the previous blog, I have explained how to gather information using Footprinting. But knowing basic information is not enough. So in this blog, I will tell you how to gather specific details of your target using Network Scanning for Ethical Hacking. If you are interested in Ethical Hacking or Cybersecurity, check out the live training by Edureka.
Network Scanning is the procedure of identifying active hosts, ports and the services used by the target application. Suppose you are an Ethical Hacker and want to find vulnerabilities in the System, you need a point in the System that you can try to attack. Network Scanning for Ethical Hacking is used to find out these points in the system that a Black Hat Hacker can use to hack the network. And then the respective teams work on improving the security of the network.
Every Organization has a Network. This network could be an internal network which consists of all the systems connected with each other, or it can be a network that’s connected to the internet. In either case, to hack the network, you will have to find a vulnerable point in the network that can be exploited. Network Scanning is used to find out such points in the network.
This Edureka “Ethical Hacking Tutorial for Beginners” video will give you an introduction to Ethical Hacking.
Think of it like this: You are an army officer and you and your team are planning to attack a terrorist lair. You have found out the location of the lair and details about the surroundings and also found ways to send the team to the lair. You can consider all this as the information you’ve gathered using Reconnaissance. Now you have to find a point through which you can enter the lair and attack the enemy. This is Network Scanning.
In simple terms, Reconnaissance is used to gather information and understand your target, and Network Scanning is a method used to find possible vulnerable points in the network through which you can hack the network.
Network scanning can be classified into two main categories:
As the name suggests, Port Scanning is a process used to find out active ports on the network. A Port Scanner sends client requests to the range of ports on the target network and then saves the details about the ports that send a response back. This is how active ports are found.
There are different types of Port Scanning. Below is a list of some of the most used ones:
Vulnerability Scanning is a type of Network Scanning for Ethical Hacking used to find out weaknesses in the network. This type of scanning identifies vulnerabilities that occur due to poor programming or misconfiguration of the network.
Now that you know what Network Scanning is, I will introduce you to some tools and tell you how to use them for Network Scanning.
Network Security Tutorial
In this section of Network Scanning for Ethical Hacking blog, I will show you how to use some Network Scanning tools. The Operating System I am using for this is Kali Linux because it comes with many in-built tools for Hacking. If you want to learn how to install Kali Linux, refer to this link.
The first tool I am going to talk about is Nmap.
Nmap is a free and open source network scanner. You can scan a network with Nmap either by using the IP address of the target:
$ nmap 1.2.3.4
Or using the hostname
$ nmap example.com
Note that it is illegal to scan the network of any organization without prior authorization by the organization. So don’t try to scan just any random network. But if we can’t scan any network without permission, then how will we learn about Nmap? Don’t worry, the Nmap Organization has provided a website for us to practice scanning using Nmap: scanme.nmap.org
Let’s try scanning this. Open a terminal in your system and run the below command:
$ nmap -v -A scanme.nmap.org
You can see how Nmap displays the open ports on the network in the result. In the above command, option ‘v‘ is for verbose output and option ‘A‘ is to detect the Operating System.
There are a lot of options that can be used with the Nmap tool to obtain different kinds of results. To understand more about using the Nmap tool, check out this Nmap tutorial.
Next tool we are going to use is Nikto.
Nikto is a Web Server Scanner that tests for dangerous files and outdated service software. And these details can be exploited and used to hack the network. Nikto is designed to scan the web server in the quickest possible time.
To use Nikto, open the terminal and run the following command:
$ nikto -host scanme.nmap.org
You should see a similar output
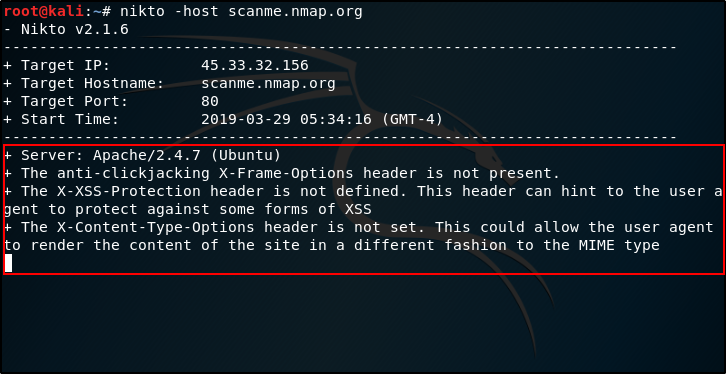
The highlighted part in the above screenshot shows the results that Nikto has found. These results are helpful to understand the weaknesses of the network or application being scanned. Once you find the weakness of the network, you can choose relevant attacks to hack the network.
Learn about the latest tools, technologies, and frameworks used in ethical hacking through this Online Ethical Hacking Certification Course .
The next tool I am going to talk about is Nessus.
Nessus is one of the most powerful vulnerability scanners available. This scanner does not come pre-installed with Kali Linux. So, before telling how to use it, I will show you how to install it.
Open a browser and go to www.tenable.com/downloads/nessus and click on “Get Activation Code“.
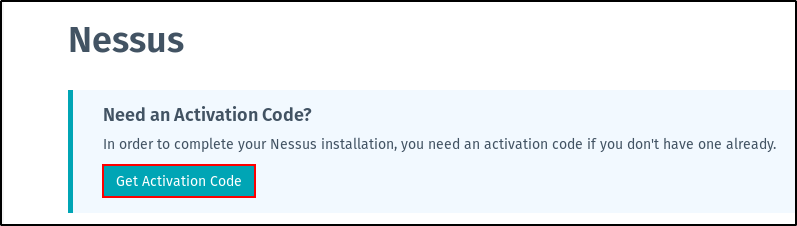
You will see two versions of Nessus: A free version(Nessus Home) and a paid version. We shall use the free version, so click on the “Register Now” button under “Nessus Home“.
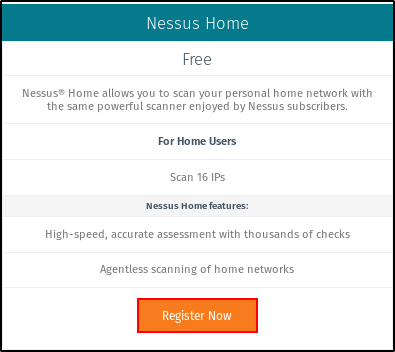
In the next page, enter your first name, last name, and Email Id. A link will be sent to your Email Id and you will be redirected to the download page.
Download a suitable file. I am downloading the .deb file for AMD64 architecture because that’s compatible for the Kali Linux I am using.

After the download is complete, open the terminal and run the following command to install Nessus:
$ cd Downloads $ dpkg -i Nessus-8.3.0-ubuntu910_amd64.deb
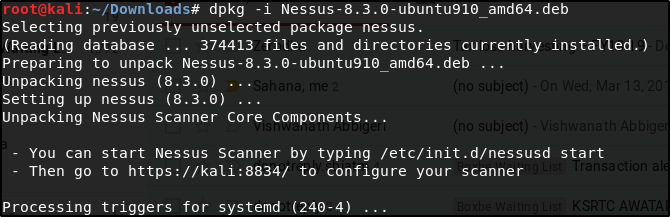
Nessus will be installed and now you will have to start the Nessus service to use it. Refer to the below command:
$ /etc/init.d/nessusd start
Once the service starts, open a web browser and go to //kali:8834/
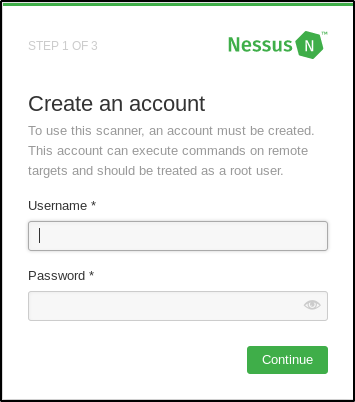
Enter a Username and a Password and in the next page, enter the Activation Code that was sent to your Email Id.
After successful activation, wait for Nessus to download necessary Plugins. Once Nessus completes the setup, you will see something like this:
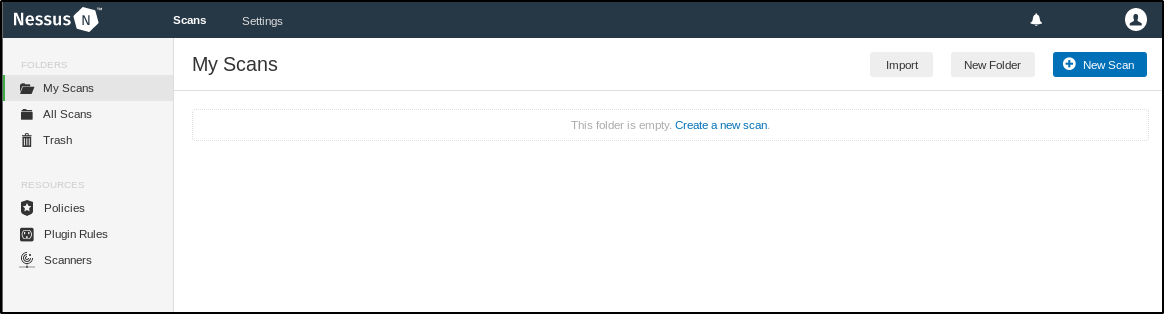
To scan a network, click on “New Scan” on the top right corner.
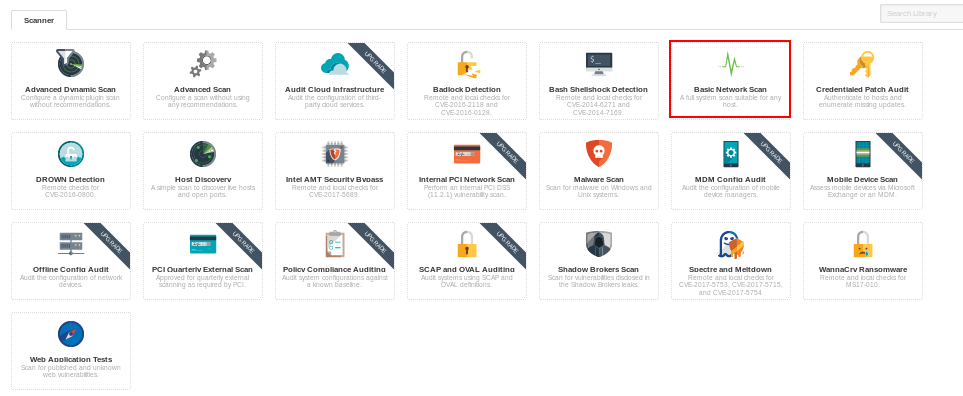
In the next page, you will see different types of scans that Nessus provides. I will choose “Basic Network Scan“.
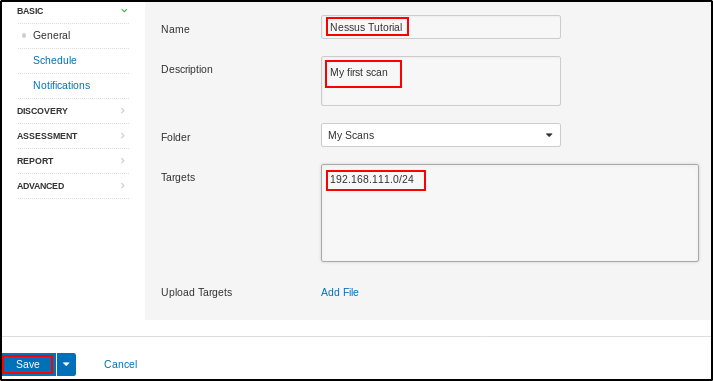
Enter the name for your scan, description, folder, and the target and click on “Save“. For this Network Scanning for Ethical Hacking tutorial, I will scan my local network.
Next, select the scan and click on the start icon.
After the scan is complete, you can see the vulnerability report under the “Vulnerabilities” tab.
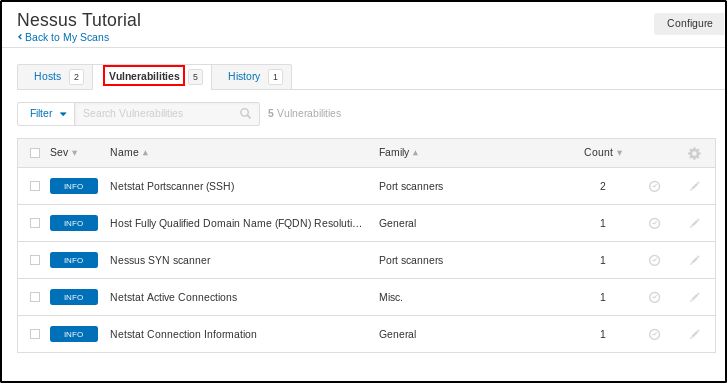
The scan results show the information and vulnerabilities found. This is how Nessus can be used for Network Scanning for Ethical Hacking.
The more details you find out about the target, the easier it will be to test for vulnerabilities. Try using more Network Scanning tools such as OpenVAS, Core Impact, Retina, etc. If you have any question, ask it on Edureka Community and we will get back to you.
Related Posts:
What is Cyber Threat Intelligence
Information gathering with Python scraping
If you wish to learn Ethical hacking , then check out our CEH V13 Certification Training course which comes with instructor-led live training and real-life project experience.. You can also take a look at our newly launched course on Comptia Security+ Course which is a first-of-a-kind official partnership between Edureka & CompTIA Security+. It offers you a chance to earn a global certification that focuses on core cybersecurity skills which are indispensable for security and network administrators.
Learn Cybersecurity the right way with Edureka’s POST-GRADUATE PROGRAM with NIT Rourkela and defend the world’s biggest companies from phishers, hackers and cyber attacks.
 Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUPedureka.co
nice