AWS Solution Architect Certification Training
- 184k Enrolled Learners
- Weekend/Weekday
- Live Class
Organizations must have control over who has permission to access their AWS resources, which resources are available, and the actions authorized users can perform. The purpose of AWS IAM is to help IT administrators manage AWS user identities and their varying levels of access to AWS resources. In this article, we will understand the features and working procedure of Identity and Access Management (IAM) in the following sequence:
AWS Identity and Access Management (IAM) is a web service that helps you securely control access to AWS resources. With IAM, you can control who is authenticated and authorized to use resources.
When you first create an AWS account, you need a single sign-in identity to access all AWS services. This identity is called the AWS account root user. You can access it by signing in with the email ID and password that you used to create the account. AWS IAM helps in performing the following tasks:
Now that you know what is IAM, let’s have a look at some of its features.
Some of the important Features of IAM include:
Now let’s move on and understand the working of Identity and Access Management.
Identity Access and Management offers the best infrastructure that is required to control all the authorization and authentication for your AWS account. Here are some of the elements of IAM infrastructure:
The principle in the AWS IAM is used to take an action on the AWS resource. The administrative IAM user is the first principle, which can allow the user for the particular services in order to assume a role. You can support the federated users to allow the application access your current AWS account.
While using the AWS management console, the API or CLI will automatically send the request to AWS. It will specify the following informations:
It is one of the most commonly used principles which is used to sign in for AWS while sending the request to it. However, it also consists of the alternate services like Amazon S3 which will allow requests from the unknown users. In order to authenticate from the console, you need to sign in with your login credentials like username and password. But to authenticate you need to provide the secret and access key to them along with the required additional security information.
While authorizing the IAM values that are raised from the request will context to check all the matching policies and evaluate whether it is allowed or denied the respective request. All the policies are stored in IAM as JSON documents and offer the specified permission for the other resources. AWS IAM automatically checks all the policies which particularly match the context of all your requests. If the single action is denied then the IAM denies the entire request and regret to evaluate the remaining ones, which is called as an explicit deny. The following are some of the evaluation logic rules for IAM:
After processing your request authorization or unauthenticated automatically, AWS approves your action in the form of request. Here all the actions are defined by services and things can be done by resources such as creating, editing, deleting and viewing. In order to allow the principle of action, we need to include all the required actions into policy without affecting the existing resource.
After getting the AWS approvals all the actions in your request can be done based on the related resources that contain in your account. Generally, a resource is called an entity which exists particularly within the services. These resource services can be defined as a set of activities which is performed particularly on each and every resource. If you want to create one request, first you need to perform the unrelated action that cannot be denied.
Now let’s take an example and understand the concept of Identity Access Management better.
To understand the concept of Identity and Access Management (IAM), let’s take an example. Suppose a person has a start-up with 3-4 members and hosted the Application over Amazon. Since it’s a small organization everybody would have access to Amazon where they can configure and perform other activities with their Amazon Account. Once the team size grows with a set of people in each department, he would not prefer to give full access to Amazon Web services, as they are all employees and the data needs to be protected. In this case, it would be advisable to create a few Amazon web service accounts called the IAM users. The advantage here is that we can control in what domain they can work.
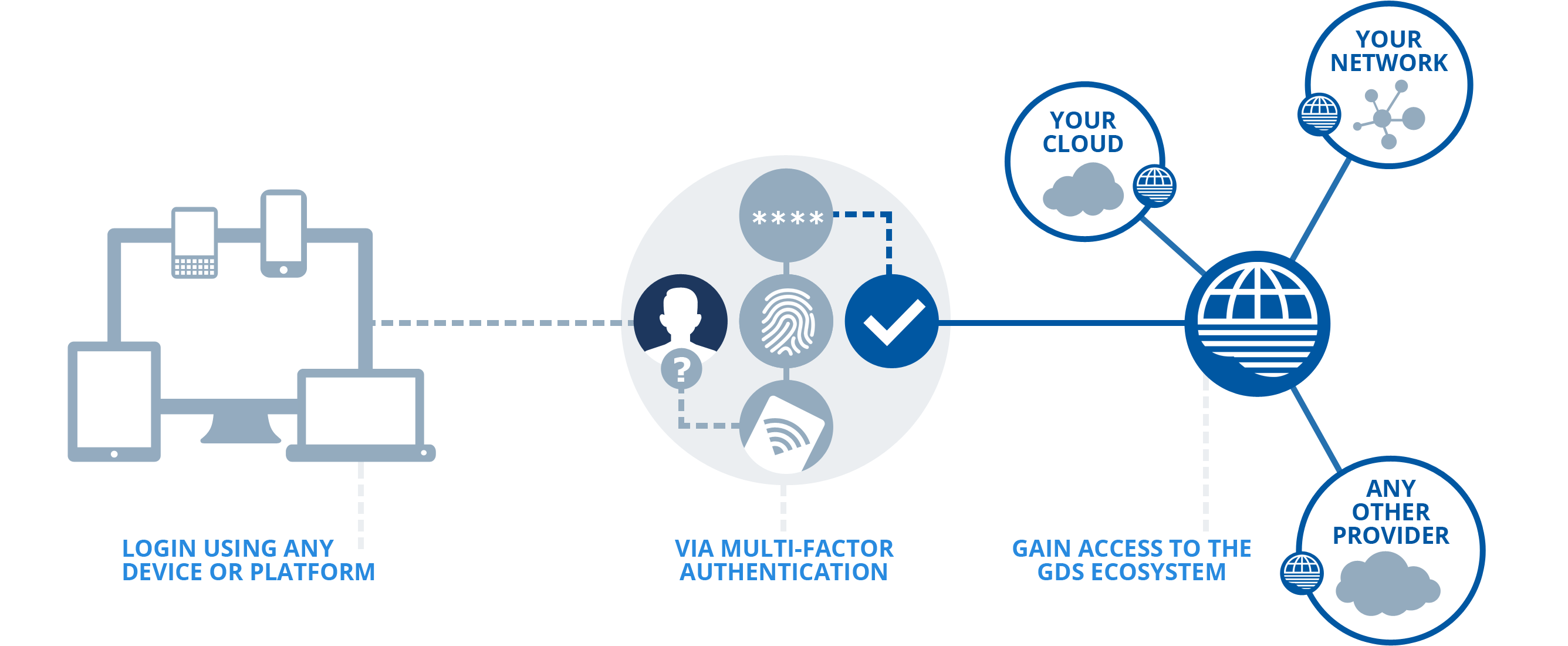
Now, if the team grows to 4,000 people with various tasks and departments. The best solution would be that Amazon supports the single sign in with the directory services. Amazon provides service supported by SAML based authentication. It would not ask for any credential when somebody from the organisation logs in to the organisation machine. It would then to the Amazon Portal and it would show services that the particular user is allowed to use. The biggest advantage of using IAM is that there is no need to create multiple users but implement a simple sign-in.
With this, we have come to the end of our article. I hope you understood what is Identity and Access Management in AWS and how it works.
If you have decided to prepare for an AWS certification, you should check out our courses on AWS Certification. Got a question for us? Please mention it in the comments section of “Identity and Access Management” and we will get back to you.
 Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUPedureka.co
Using this Management, can we provide control in uploading data for users?
Your post, regarding to IAM is very nice.
Great Article..It was very informative..I need more details from your side..include some tips..I am working in Erp Development Companies In India