Cyber Security and Ethical Hacking Internship ...
- 15k Enrolled Learners
- Weekend/Weekday
- Live Class
This blog will be about how to start with Ethical Hacking. I will be discussing the phase of Footprinting, and some ways to gather information about the application you want to test for Vulnerabilities. For learning the other phases in detail, check out Edureka’s Cyber Security certification Course
Imagine you are a well known Ethical Hacker and you get a job to check a Web Application for vulnerabilities. You get the name of the organization whose website you have to test. How would you start testing the website for vulnerabilities? You would start by gathering information about that website. This is what Footprinting is.
Footprinting is a part of the Reconnaissance phase of Ethical Hacking in which you gather information about the system/ application. The main aim of Footprinting is to gather as much information as possible about the system/ application to narrow down the areas and techniques of attack.
Most of the people find Footprinting boring, but it is a very important part of Ethical Hacking. And the next section will tell you why.
Footprinting is considered one of the most important phases of Ethical Hacking. Let’s take a movie plot for example. Suppose you are watching a Bank robbery movie, there are people who have planned to rob a bank. Movies like Ocean’s Eleven, The Italian Job or Fast and Furious, do the characters directly buy guns and masks and enter the bank to rob it? No! If they did this, they wouldn’t be able to rob the bank successfully.
So what do they do before robbing the bank? They make a proper plan on how to enter the bank, how to handle the security, and prepare an escape plan. And to plan the robbery, they need to observe certain things about the bank, the way it operates, how the security works, etc. Knowing about the bank plays an important role in making the plan.
Similarly, knowing about the system/ application is very important for ethical hacking because it will let you know what type of vulnerabilities can be found and what attacks are suitable.
It’s time to understand a little about the different types of Footprinting.
Related Post : What is Cyber Threat Intelligence
Similar to Reconnaissance, Footprinting can be divided into two types:
Active Footprinting is the type of Footprinting where you gather information about the system/ application by directly interacting with the system. When you use Active Footprinting, there is a high chance that some information like your IP address is saved by the system you are trying to gather the information about.
In the case of Passive Footprinting, you gather information without interacting with the system/ application you are trying to know about. You gather information through search engines or public records. When you use Passive Footprinting, there is no way that the system would save your IP address.
Now that you have understood the basics of Footprinting, without further delay, let’s get to the hands-on part of Footprinting
Looking for a challenging and rewarding career in cybersecurity? Enroll in the CISSP Online Training.
Related Post : What Is Network Forensics?
Ethical Hacking Full Course – Learn Ethical Hacking in 10 Hours
In this section, I will show you some methods to gather information. I will be using Kali Linux Operating System for this. If you don’t have Kali Linux, you can visit this link to learn how to install Kali Linux.
Learn about the latest tools, technologies, and frameworks used in ethical hacking through this Ethical Hacking Internship.
In this blog, we will try to gather information about Edureka Community. Suppose you don’t know anything about Edureka Community, how would you start gathering information? The first step is to use a search engine.
Open a browser and search for “Edureka Community”.
You will find the URL of Edureka Community i.e., www.edureka.co/community. This is the first piece of information you have found.
Using the URL of the website, you can find the IP address of the website by pinging to it.
Related Post Role and automation of WHOIS data in footprinting
To find the IP address of Edureka Community website, open the terminal and run the below command:
$ ping www.edureka.co
Wait, we wanted to find the IP address of www.edureka.co/community, then why did we ping to www.edureka.co?
That is because Edureka Community is under the www.edureka.co domain and this web application is structured such that the IP address of the community is the same as that of the domain.
Run the above-mentioned command and you should see a similar output.
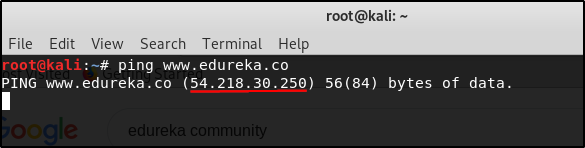
You can see that we found the IP address of Edureka Community. The IP address is 54.218.30.250.
The IP address is just a tiny piece of information about the website. To get more information, we will use Whois Lookup.
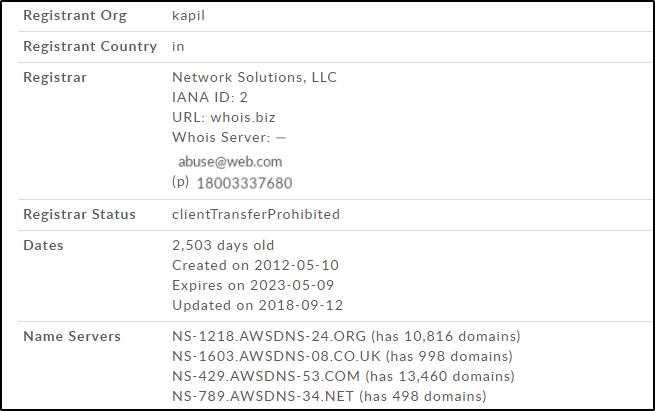
Whois Lookup is a tool used to find out information such as DNS, domain names, name servers, IP addresses, etc. Let’s use Whois Lookup to find some more information about the Edureka Community website, open a browser and go to http://whois.domaintools.com/
Enter the website name (or IP address) and click “Search“

This search will display various information about the website.
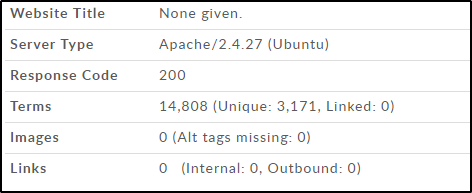
You can see in the above screenshot that the Server type being used by Edureka Community is Apache/2.4.27. This gives a point for an Ethical Hacker to start testing. And also, you can limit your attacks only to those that are applicable to Apache/2.4.27 Server.
This is how Footprinting helps an Ethical Hacker. The more information you gather using Footprinting, the more places you get to look for vulnerabilities. Explore some more ways to find information and see what other information you can gather using Footprinting. If you have a question, ask on Edureka Community and we will get back to you.
Related Post Reverse lookups for footprinting
If you wish to learn Cybersecurity and build a colorful career in Cybersecurity, then check out our Cyber Security Course Online which comes with instructor-led live training and real-life project experience. This training will help you understand Cybersecurity in depth and help you achieve mastery over the subject.Now that you’ve got an idea of what Footprinting is and why it is important. If you are excited to learn about footprinting in ethical hacking, explore our CEH Certification Course
You can also take a look at our newly launched course on CompTIA Security+ Certification Training which is a first-of-a-kind official partnership between Edureka & CompTIA Security+. It offers you a chance to earn a global certification that focuses on core cybersecurity skills which are indispensable for security and network administrators.
Learn Cybersecurity the right way with Edureka’s POST-GRADUATE PROGRAM with NIT Rourkela and defend the world’s biggest companies from phishers, hackers and cyber attacks.
 Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUPedureka.co