Cyber Security and Ethical Hacking Internship ...
- 15k Enrolled Learners
- Weekend/Weekday
- Live Class
Data is the most valuable asset, which is the reason why data security has become an international agenda. Data breaches and security failures can put the world economy at risk. Realizing the need for national and economic security, the President of US issued an Executive Order to develop a Cybersecurity Framework to help reduce cyber risks. Dive deeper into the feed to know more about the Frame.
Implementing the Framework is effective because:
his Edureka video on “What is Cyber Security” gives an introduction to the Cyber Security world and talks about its basic concepts.
Developed through coordinated effort amongst business and government, the intentional Framework comprises of measures, rules, and practices to showcase the safety of imperative foundation. The organized, adaptable, repeatable, and effective approach of the Framework helps house proprietors and administrators of critical foundation to oversee cybersecurity-related hazard.
Check out our new CEH (v13) – Certified Ethical Hacker course to learn the in-depth concepts of ethical hacking and get skilled.
The most frequently adopted frameworks are:
Ready to take your career in cybersecurity to the next level? CISSP Certification is the way!
There are three key components: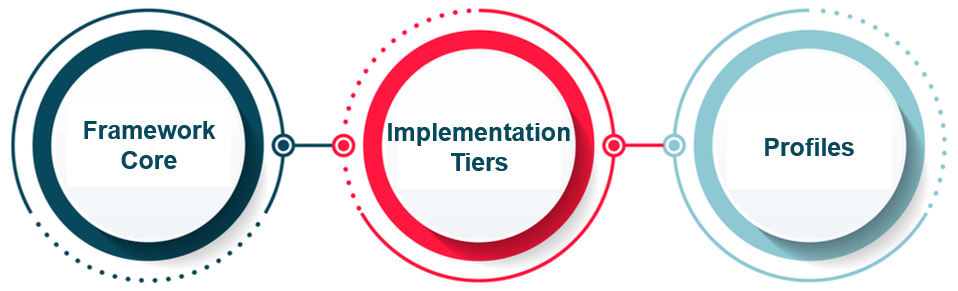
Framework Core: It gives an arrangement of required Cybersecurity exercises and results utilizing normal understandable language. The Core guides associations in overseeing and decreasing their Cybersecurity chances in a way that supplements an association’s current Cybersecurity and risk management processes.
Implementation tiers: It helps associations by giving setting on how an association sees Cybersecurity risk management. The tiers manage associations to consider the suitable level of thoroughness for their cybersecurity program and are regularly utilized as a specialized device to talk about hazard hunger, mission need, and spending plan.
Profiles: Profiles are an association’s novel arrangement of their organizational prerequisites and goals, and assets against the coveted results of the Framework Core. Profiles are principally used to recognize and organize open doors for enhancing Cybersecurity at an association.
The Functions are the largest amount of deliberation incorporated into the Framework. They go about as the foundation of the Framework Core that every single other component is sorted out around. The five functions included in the framework are: 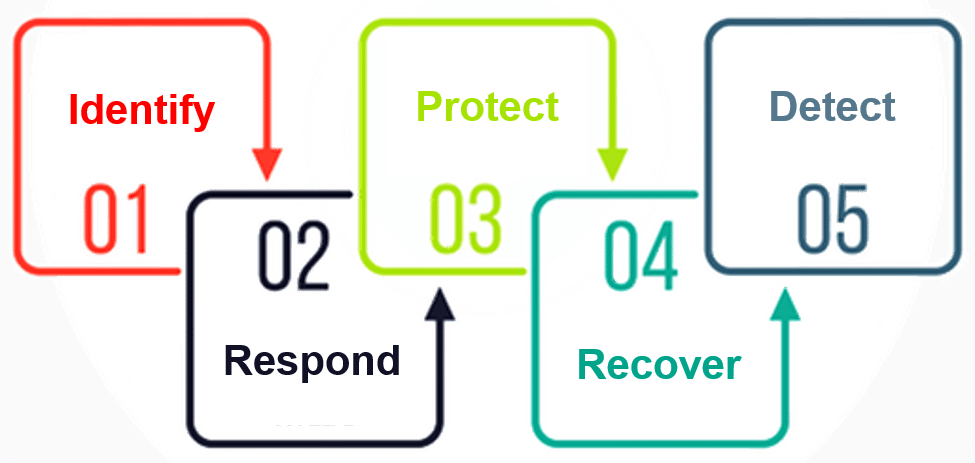
Enroll in a prestigious Cyber Security Internship program to kickstart your career.
Requirement Categories of each function
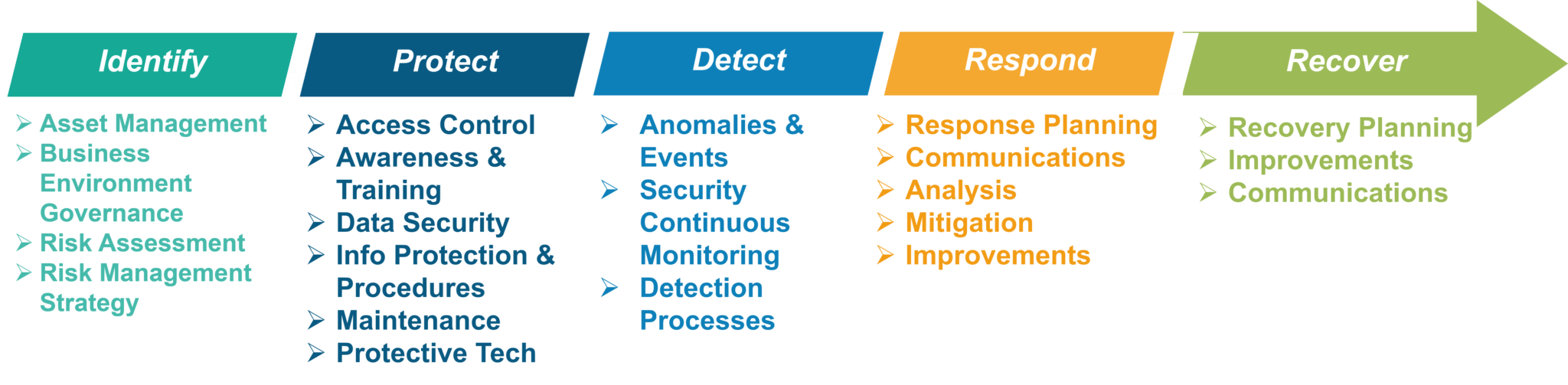
Alright, having discussed the functions and components of the framework, let’s see how these frameworks are used.
Using the framework could improve the critical infrastructure of an organization. The Framework can be implemented in stages and hence can be tailored to meet any organization’s needs. The Framework is intended to supplement, not replace, an association’s cybersecurity program and risk administration forms. 
The Cybersecurity Framework is for associations of all sizes, divisions, and developments. The framework was designed to be extremely adaptable. With built-in customization option available the framework can be modified to be used by any organizations.
A small association with a low cybersecurity spending plan, or an extensive enterprise with a major spending plan, are each ready to approach the result in a way that is attainable for them. It is this adaptability that enables the Framework to be utilized by associations which are simply beginning in setting up a cybersecurity program, while additionally offering some incentive to associations with develop programs.
In the course of recent years, NIST has been watching how the network has been utilizing the Framework. These are some regular examples that we have seen develop:
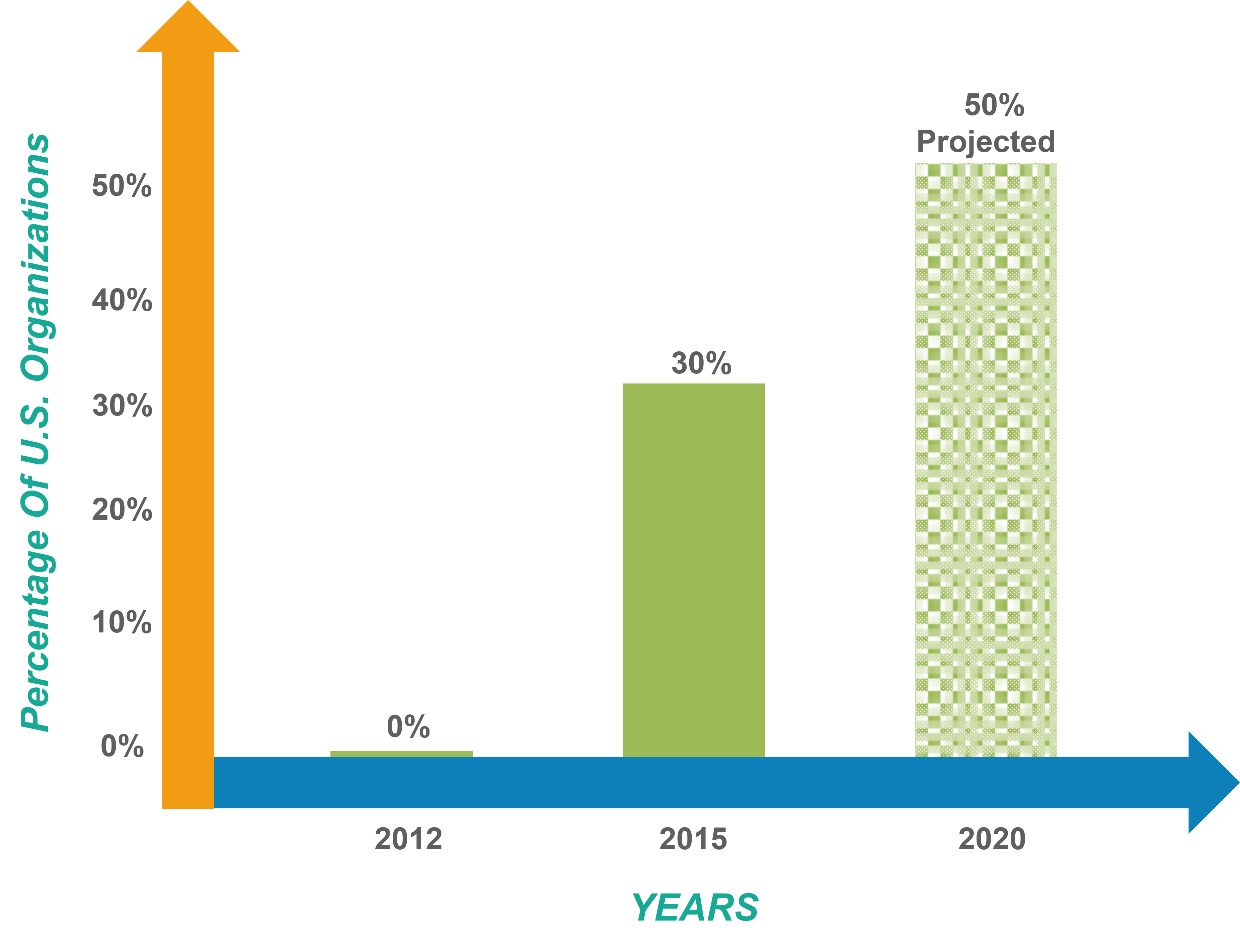
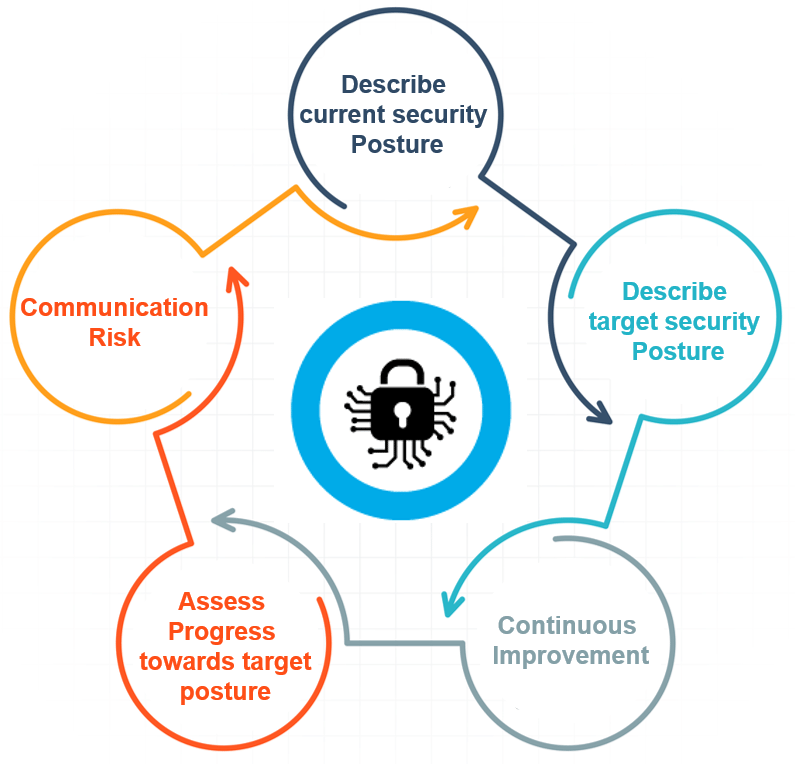
The Cybersecurity Framework defines 7 steps for establishing a cybersecurity program: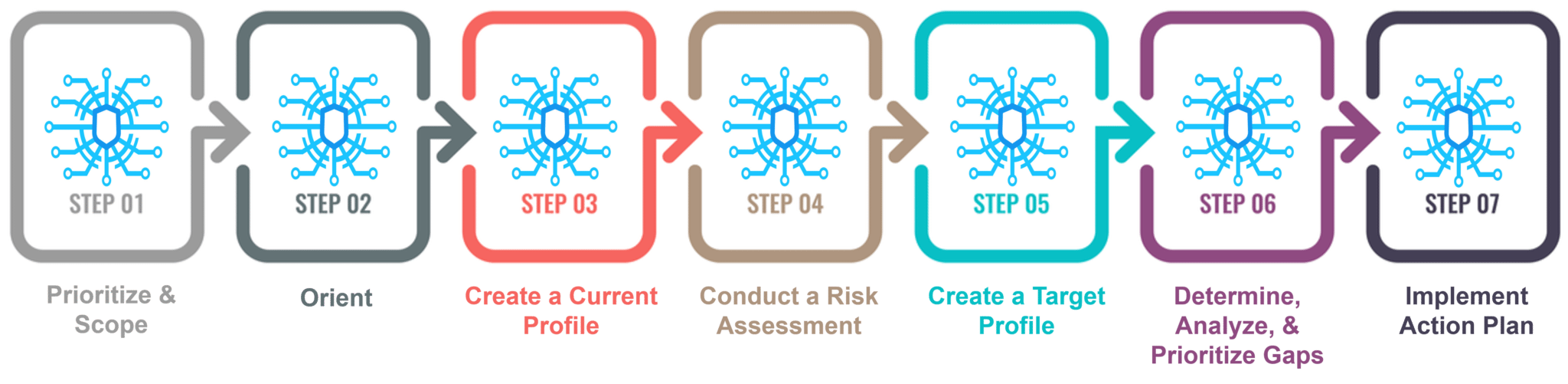 Example of Organization’s Using the Cybersecurity Framework
Example of Organization’s Using the Cybersecurity Framework
Nuclear Sector Cybersecurity Framework Implementation:
Atomic reactors in the United States have a solid reputation of cooperating to create and execute digital security principles, devices, and procedures that guarantee wellbeing, security, and unwavering quality.
The Framework is intended to be sufficiently adaptable to be utilized both by associations with developing digital security and risk administration programs and by those with less-created programs.
As a rule, implementing the Framework gives an instrument to associations to:
Here’s how the Cybersecurity Framework was used to demonstrate how cybersecurity practices at U.S. nuclear power plants align to the Framework.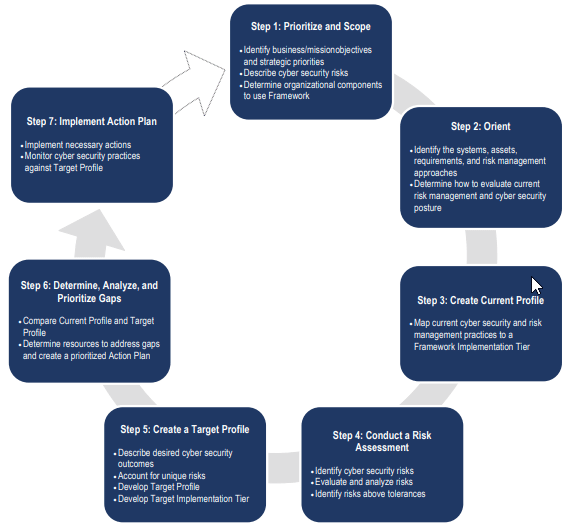
I hope this blog was helpful and now you have a basic understanding of Cybersecurity Frameworks. Stay tuned for more blogs by Edureka.
If you wish to learn Cybersecurity and build a colorful career in cybersecurity, then check out our Cyber Security Certification Training which comes with instructor-led live training and real-life project experience or join our Masters in Cyber Security. This training will help you understand Cybersecurity in depth and help you achieve mastery over the subject.
You can also take a look at our newly launched course on CompTIA Security+ Training Course which is a first-of-a-kind official partnership between Edureka & CompTIA Security+. It offers you a chance to earn a global certification that focuses on core cybersecurity skills which are indispensable for security and network administrators.
Got a question for us? Please mention it in the comments section and we will get back to you or join our Cyber Security training in Salem.
 Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUPedureka.co
great video!!!!!